Search N5 Net Software Repository:
Search Files
Sponsor:
Browse:
- Audio & Multimedia (1621)
- Business (4269)
- Communications (1275)
- Desktop (188)
- Development (613)
- Education (177)
- Games & Entertainment (714)
- Graphic Apps (690)
- Home & Hobby (107)
- Network & Internet (577)
- Security & Privacy (529)
- Servers (65)
- System Utilities (11779)
- Web Development (292)
Areas Of Interest
Authors Area
Are you a software author? Take a look at our Author Resource Center where you will find marketing tools, software specifically created for promoting your software and a ton of other helpful resources.
Cell Phone Tracker 1.2
With Cell Phone Tracker, you can monitor how your child uses the phone. It is a monitoring tool that allows you to spy on what they are doing on the device. Although the focus is on parental controls, the Cell Phone Tracker can be used in many other situations. By using Cell Phone Tracker, even if you are not with your children/family, you can monitor and protect them at any time. The online world is as complicated as real life, full of dangers, such as those who commit sex offenders, thugs, and ordinary bad guys. You can track them without them knowing and come to help on time if needed. You may want to follow your worker activity. Is there an employee you suspect of stealing company secrets or working to pass information to a competitor? You can keep tabs on their phone or tablet use with Cell Phone Tracker. If they are indeed passing on confidential information, then you can use their phone or table to catch them in the act and confront them with evidence.
Specifications:
Version: 1.2 |
Download
|
Similar Products:
Security & Privacy :: Other
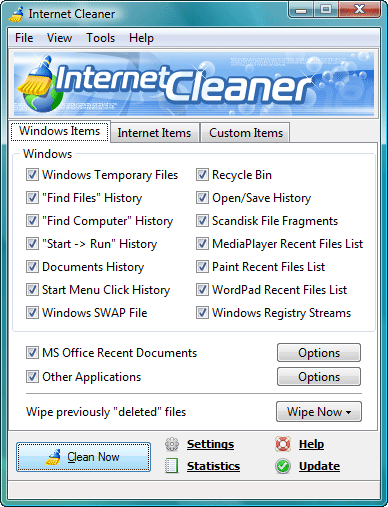 Internet Cleaner helps you remove all traces of your online and offline activity, including the list of recently visited sites, browser cache and cookies (IE, Firefox, AOL, MSN, Mozilla, Opera and Netscape Navigator are supported), lists of recent documents in various applications (MS Office, Paint, Media Player, WordPad, Acrobat Reader, ACDSee and more) and protect your privacy by erasing the traces of Messenger, Email, News, P2P programs.
Internet Cleaner helps you remove all traces of your online and offline activity, including the list of recently visited sites, browser cache and cookies (IE, Firefox, AOL, MSN, Mozilla, Opera and Netscape Navigator are supported), lists of recent documents in various applications (MS Office, Paint, Media Player, WordPad, Acrobat Reader, ACDSee and more) and protect your privacy by erasing the traces of Messenger, Email, News, P2P programs.
Windows | Shareware
Read More
Security & Privacy :: Other
 A program for secure file deletion which overwrites data in specified files so that the data cannot be recovered by any means. A single file can be purged or, in batch mode, multiple files. Selected subfolders of a folder can be purged. The user can specify the type of purge. Purge speed can be tested for an estimation of time required. Can wipe files older than a specified date. Can wipe files in the Windows 7 and 8 Recycle Bin.
A program for secure file deletion which overwrites data in specified files so that the data cannot be recovered by any means. A single file can be purged or, in batch mode, multiple files. Selected subfolders of a folder can be purged. The user can specify the type of purge. Purge speed can be tested for an estimation of time required. Can wipe files older than a specified date. Can wipe files in the Windows 7 and 8 Recycle Bin.
Windows | Shareware
Read More
Security & Privacy :: Other
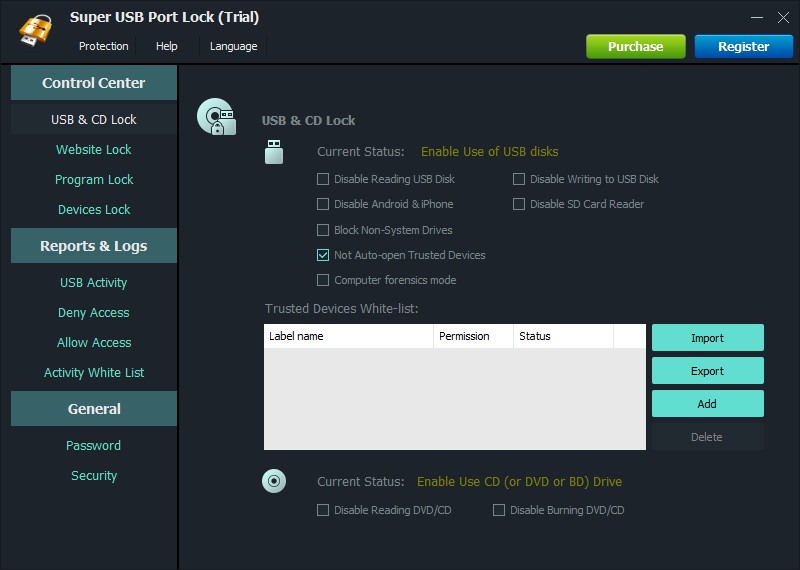 Super USB Port Lock prevents data leaks through devices like USB drives, phones, tablets and other devices that are attached to your computer. It also prevents data leaks through any websites and programs.
Super USB Port Lock prevents data leaks through devices like USB drives, phones, tablets and other devices that are attached to your computer. It also prevents data leaks through any websites and programs.
Windows | Shareware
Read More
Security & Privacy :: Other
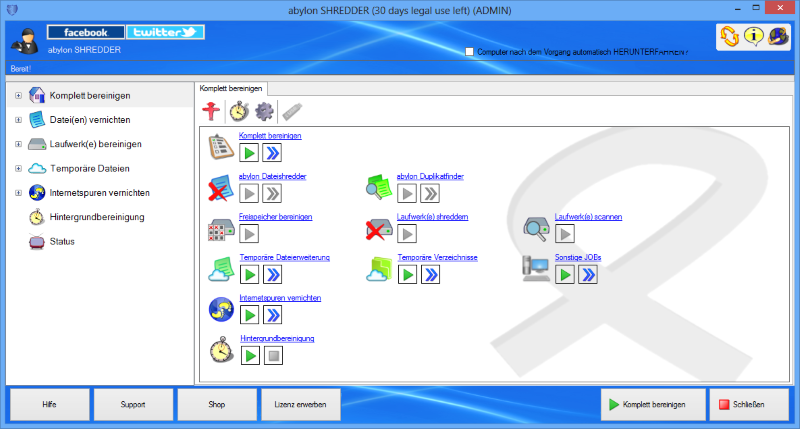 The deletion of files with the windows recycle bin removes only the references to the files, without real clearing. In contrast to this the software abylon SHREDDER overwrite the data up to 35 times (Peter Gutman method). Afterwards the data can not be reconstructed any longer. The same goes for free space, clustertips, surf traces of the browser, file names, duplicate files or full drives.
The deletion of files with the windows recycle bin removes only the references to the files, without real clearing. In contrast to this the software abylon SHREDDER overwrite the data up to 35 times (Peter Gutman method). Afterwards the data can not be reconstructed any longer. The same goes for free space, clustertips, surf traces of the browser, file names, duplicate files or full drives.
Windows | Shareware
Read More



