Search N5 Net Software Repository:
Search Files
Sponsor:
Browse:
- Audio & Multimedia (1621)
- Business (4269)
- Communications (1275)
- Desktop (188)
- Development (613)
- Education (177)
- Games & Entertainment (714)
- Graphic Apps (690)
- Home & Hobby (107)
- Network & Internet (577)
- Security & Privacy (529)
- Servers (65)
- System Utilities (11779)
- Web Development (292)
Areas Of Interest
Authors Area
Are you a software author? Take a look at our Author Resource Center where you will find marketing tools, software specifically created for promoting your software and a ton of other helpful resources.
Activity and Authentication Analyzer 1.64.0.11
Security & Privacy :: Access Control
Your PC keeps records of both your online and off-line activity. Any of the Web Pages, Movies, Pictures, Sounds, E-mail and Everything Else you have ever viewed could easily be recovered - even after many years passed! This is a serious threat to the legitimate user's privacy. Activity and Authentication Analyzer is a solution to this problem. AAAnalyzer is the powerful security software, which has been primarily destined to comprehensive search, analysis, the user activity traces left after work. The activity analysis and authentication or how it is called in brief ?statistics?, as the method of information (intelligence data) collection is applied either for the preliminary exploring or when the access to information (posted message, telephone talk) is impossible or unwanted. As applied to the computer security topics the activity analysis and authentication is performed when it is impossible to get documents? copies, which user worked on, for example, stored either on ciphered or dismounted disk containers. Nevertheless, ?nothing is disappeared without any trace? and it is possible, therefore, to disclose much useful data from the documents? names, Internet addresses, which were visited, the applications? names which were launched or file names which were searched, last user?s logon name. Windows 95/98/NT/2000/XP/2003/Vista/7/8/8.1/10/11 has the system registry database, which is useful, for the first, to the very OS, but, for the second, for keeping many traces (evidences in other words) left by routine work and for either exploration, or for reconstruction of user?s activity. Its built-in functionality allows to search the traces left in system registry, stored in registry keys related to the activity and authentication analysis
Specifications:
Version: 1.64.0.11 |
Download
|
Similar Products:
Security & Privacy :: Access Control
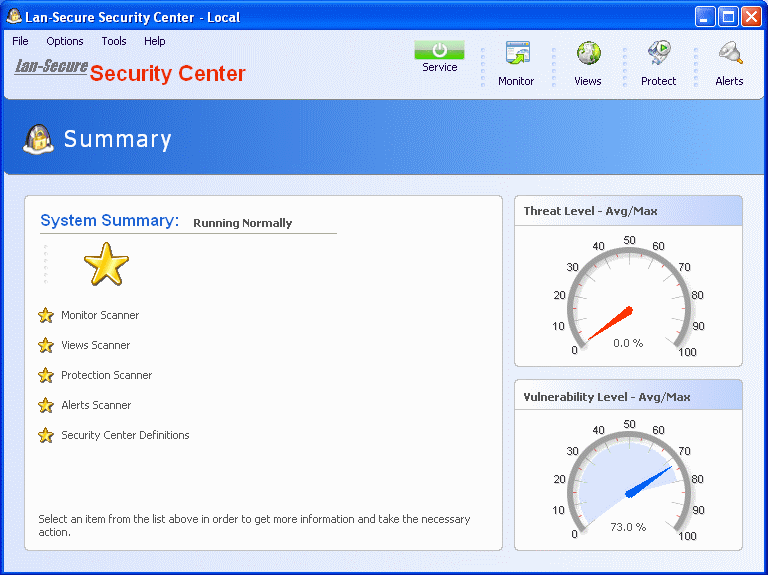 Security Center is network security software for real-time intrusion detection IDS and prevention IPS that helps to protect networks from potential intruders, unauthorized connections and malicious activities. The unique network monitoring engine provide real-time threats and vulnerabilities discovery. The built-in manual and automatic protection rules enable network policy enforcement and proactive blocking of network nodes.
Security Center is network security software for real-time intrusion detection IDS and prevention IPS that helps to protect networks from potential intruders, unauthorized connections and malicious activities. The unique network monitoring engine provide real-time threats and vulnerabilities discovery. The built-in manual and automatic protection rules enable network policy enforcement and proactive blocking of network nodes.
Windows | Shareware
Read More
Security & Privacy :: Access Control
 Regular PDF files can be viewed by the PDF reader applications and allow people to print, copy the content or convert text to other editable files. You would find some PDFs can be accessed like regular PDFs, but you cannot print them or select and copy the text while reading. These secured PDFs which were added permissions and restrictions by document creators. PDF Unlocker Online is a free online tool designed to remove protections from PDFs.
Regular PDF files can be viewed by the PDF reader applications and allow people to print, copy the content or convert text to other editable files. You would find some PDFs can be accessed like regular PDFs, but you cannot print them or select and copy the text while reading. These secured PDFs which were added permissions and restrictions by document creators. PDF Unlocker Online is a free online tool designed to remove protections from PDFs.
Windows MAC Linux | Freeware
Read More
Security & Privacy :: Access Control
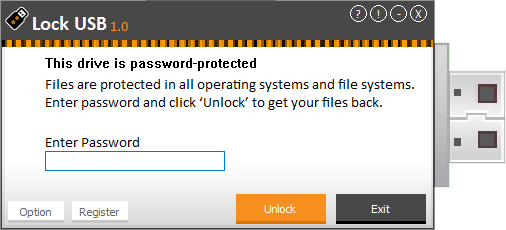 Lock USB password-protects your USB and external drives in seconds and is the only product that keeps them locked on all operating systems including Windows/Mac/Linux and file systems like FAT32/NTFS/exFAT.
Lock USB password-protects your USB and external drives in seconds and is the only product that keeps them locked on all operating systems including Windows/Mac/Linux and file systems like FAT32/NTFS/exFAT.
Windows | Shareware
Read More
Security & Privacy :: Access Control
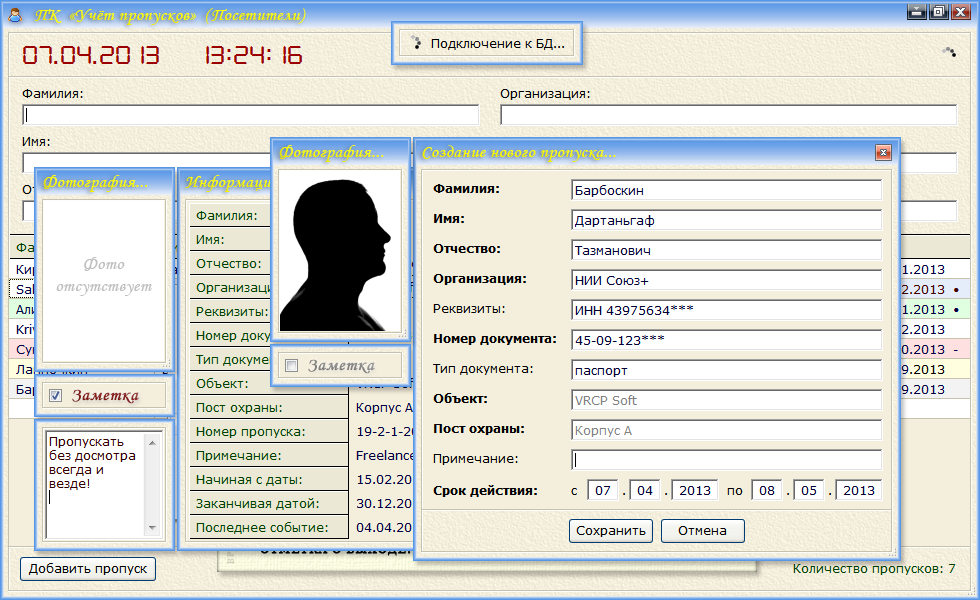 The program complex 'Accounting of Admissions' is intended for the organization of the automated work with the electronic database containing information on admissions (constant, temporary or single) on the protected objects for the purpose of implementation of additional control of the entering/leaving persons, and also the driving/leaving motor transport.
The program complex 'Accounting of Admissions' is intended for the organization of the automated work with the electronic database containing information on admissions (constant, temporary or single) on the protected objects for the purpose of implementation of additional control of the entering/leaving persons, and also the driving/leaving motor transport.
Windows | Freeware
Read More




