Search N5 Net Software Repository:
Search Files
Sponsor:
Browse:
- Audio & Multimedia (1621)
- Business (4269)
- Communications (1275)
- Desktop (188)
- Development (613)
- Education (177)
- Games & Entertainment (714)
- Graphic Apps (690)
- Home & Hobby (107)
- Network & Internet (577)
- Security & Privacy (529)
- Servers (65)
- System Utilities (11779)
- Web Development (292)
Areas Of Interest
Authors Area
Are you a software author? Take a look at our Author Resource Center where you will find marketing tools, software specifically created for promoting your software and a ton of other helpful resources.
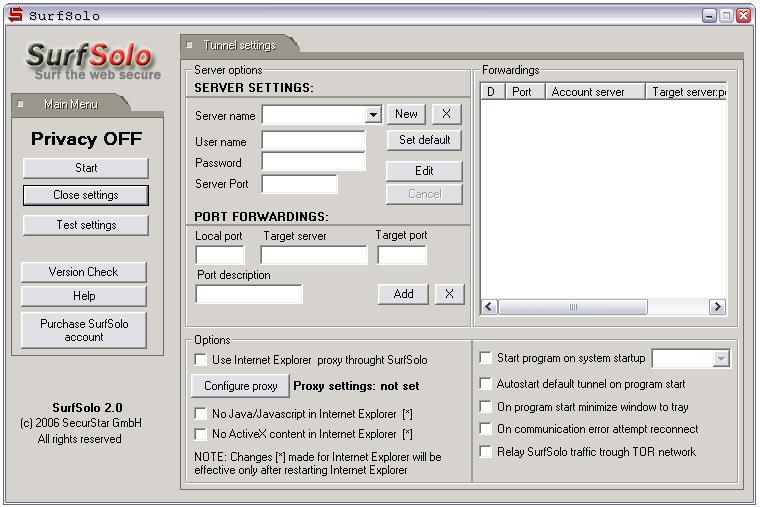
SurfSolo 2.0
No one knows more about ?surfing? and downloading habits than your ISP (Internet Service Provider). The ISP is able to know who you are, every site you visit, every page you view, and every file you download. How this happens? Every time you are connected on the Internet your ISP gives you an IP number that is a unique address which identifies you from the other computers on the network living you vunerable to any attacks from hackers or eavesdroppers. SurfSolo was created to protect you from those problems. Powerful software that allows the user to get totally anonymous and at the same time protects the data exchange on the Internet.The software provides a direct encrypted link(by using SSH Protocol) with one of the world wide SecurStar high bandwidth security proxy servers. ?SSH protocol (Secure Shell protocol)? which makes the connection encrypted from your personal computer to any website. A protocol says which format the data is going to be sent and which rules will be applied. The SSH protocol creates a ?virtual tunnel?, in such a way you are totally invisible from any kind of monitoring. If someone tries to track your IP number, it will recognize only our SecurStar server's IP, so it would be impossible to track your personal IP number. The SurfSolo also provides free e-mail account (no mailbox size limit). Sending emails from it will not reveal your personal IP number. At the moment SecurStar has 5 proxy servers available around the world (Malaysia, Hong Kong, Germany, Holland and Czech Republic).When the customer purchases the software he can choose one of the Proxy servers available.
Specifications:
Version: 2.0 |
Download
|
Similar Products:
Security & Privacy :: Other
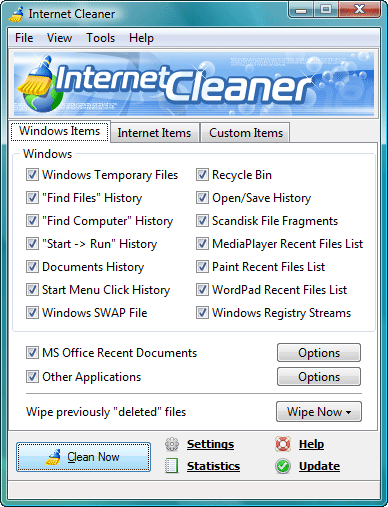 Internet Cleaner helps you remove all traces of your online and offline activity, including the list of recently visited sites, browser cache and cookies (IE, Firefox, AOL, MSN, Mozilla, Opera and Netscape Navigator are supported), lists of recent documents in various applications (MS Office, Paint, Media Player, WordPad, Acrobat Reader, ACDSee and more) and protect your privacy by erasing the traces of Messenger, Email, News, P2P programs.
Internet Cleaner helps you remove all traces of your online and offline activity, including the list of recently visited sites, browser cache and cookies (IE, Firefox, AOL, MSN, Mozilla, Opera and Netscape Navigator are supported), lists of recent documents in various applications (MS Office, Paint, Media Player, WordPad, Acrobat Reader, ACDSee and more) and protect your privacy by erasing the traces of Messenger, Email, News, P2P programs.
Windows | Shareware
Read More
Security & Privacy :: Other
 A program for secure file deletion which overwrites data in specified files so that the data cannot be recovered by any means. A single file can be purged or, in batch mode, multiple files. Selected subfolders of a folder can be purged. The user can specify the type of purge. Purge speed can be tested for an estimation of time required. Can wipe files older than a specified date. Can wipe files in the Windows 7 and 8 Recycle Bin.
A program for secure file deletion which overwrites data in specified files so that the data cannot be recovered by any means. A single file can be purged or, in batch mode, multiple files. Selected subfolders of a folder can be purged. The user can specify the type of purge. Purge speed can be tested for an estimation of time required. Can wipe files older than a specified date. Can wipe files in the Windows 7 and 8 Recycle Bin.
Windows | Shareware
Read More
Security & Privacy :: Other
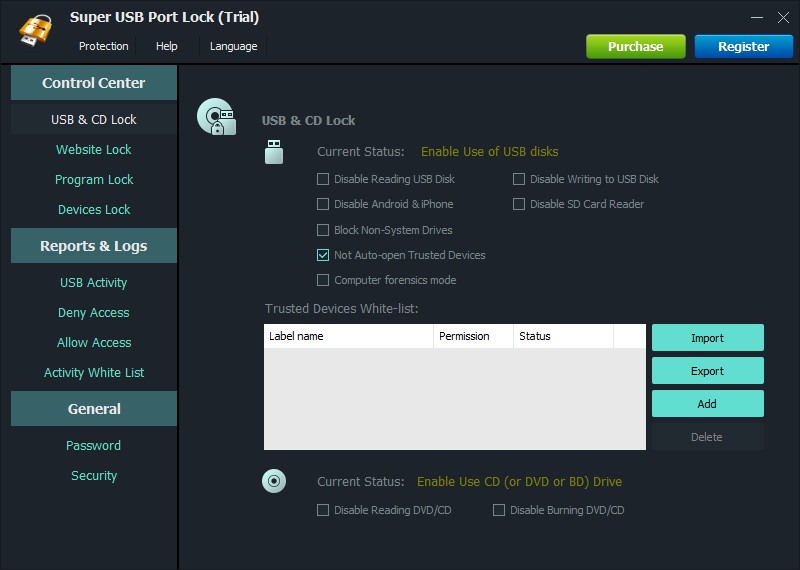 Super USB Port Lock prevents data leaks through devices like USB drives, phones, tablets and other devices that are attached to your computer. It also prevents data leaks through any websites and programs.
Super USB Port Lock prevents data leaks through devices like USB drives, phones, tablets and other devices that are attached to your computer. It also prevents data leaks through any websites and programs.
Windows | Shareware
Read More
Security & Privacy :: Other
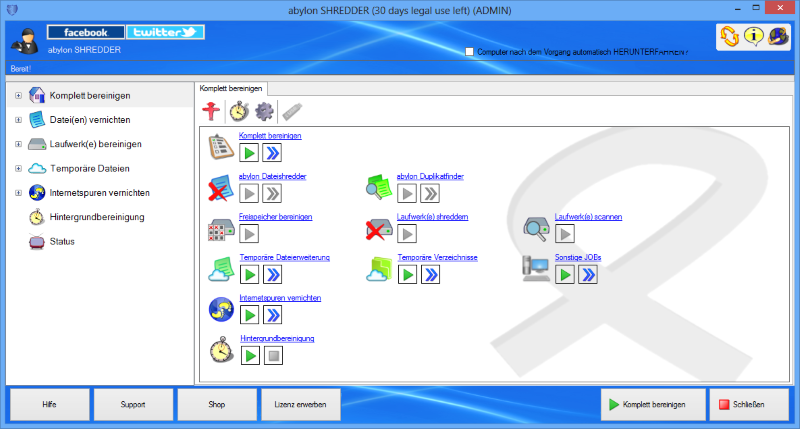 The deletion of files with the windows recycle bin removes only the references to the files, without real clearing. In contrast to this the software abylon SHREDDER overwrite the data up to 35 times (Peter Gutman method). Afterwards the data can not be reconstructed any longer. The same goes for free space, clustertips, surf traces of the browser, file names, duplicate files or full drives.
The deletion of files with the windows recycle bin removes only the references to the files, without real clearing. In contrast to this the software abylon SHREDDER overwrite the data up to 35 times (Peter Gutman method). Afterwards the data can not be reconstructed any longer. The same goes for free space, clustertips, surf traces of the browser, file names, duplicate files or full drives.
Windows | Shareware
Read More